
Clickjacking, also known as UI Redressing, is a type of cyber vulnerability where a user is tricked into clicking something different from what they think they’re clicking. When this happens embedded code or script executes without the user’s knowledge performing undesired actions.
Web pages become clickjacked when a transparent HTML page is placed atop the genuine page (the genuine page becomes “hidden” behind or “re-dressed” by the transparent page). The transparent clickjack page contains hidden code or script which is strategically placed directly over an action item on the genuine page. The user believes they are clicking on something safe from the hidden page, like a button or link, but in reality they’re clicking on a link on the clickjack page.
For example, imagine an attacker builds a web page that has a button on it that says “click here for a free iPod”. On top of that page the attacker has loaded an iframe with your email account and has lined up the “delete all messages” button (which is now invisible) exactly on top of the “free iPod” button. When the user clicks on what looks like the “free iPod” button they are actually clicking on the invisible “delete all messages” button. In essence the attacker has “hijacked” the user’s click, hence the name “Clickjacking”. (link to this example)
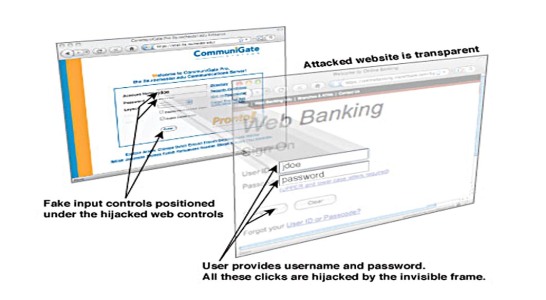
When this occurs the code attempts to do something like some of these examples:
- Make the user a follower of someone on Twitter or Facebook
- Share or like links on Facebook
- Click a Google AdSense ad to generate pay-per-click revenue
- Play a YouTube video to gain views
- Download and run malware on your computer
- Make a user’s social networking profile public
- Enable the user’s webcam or microphone
- Buy something from Amazon

How is Clickjacking Prevented?
There are two main ways to prevent clickjacking:
- Sending instructions to the browser to not allow framing from other domains
- This is a client-side measure where the user installs an add-on to their browser or uses a browser that ensures all content is visible
- Putting code in the web page that specifies how to handle the page when it is framed by another website
- This is a server-side measure where the page developer or website owner specifies how pages should be displayed when they’re placed within a frame on another site
- The two most common ways to detect and prevent clickjacking are:
- By setting an X-Frame Options HTTP header
- Bay adding JavaScript code that attempts to detect if the page is being opened in an iframe
- This type of protection is respected by modern browsers, but not by legacy browsers (older browser versions)
- In order to protect against clickjacking in legacy browsers some HTML markup and JavaScript code must be added to the page itself
Salesforce Security Measures to Prevent ClickJacking
- Clickjack protection measures need to be considered for both Salesforce orgs and community sites such as Sites.com and Force.com sites
- Salesforce uses both X-Frame Options and “frame-busting” scripts
- Visualforce pages set to API version 26.0 or earlier that do not render the standard Salesforce header (the page’s showHeader attribute is set to false) do not include HTML markup and JavaScript code to prevent clickjacking in legacy browsers
- The Summer ’17 release critical update added two new security settings
- When the settings to protect VF pages are enabled, HTML markup and JavaScript code is added to the page if necessary, regardless of the API version
Clickjack Protection Controls for an Org
- All standard Salesforce pages have clickjack protection enabled by default. (Clickjack protection was automatically enabled for all non-Setup Salesforce pages as a critical update in the Spring ’14 release.)
- Administrators have control over how Visualforce pages in an org are handled:
- Enable clickjack protection for customer Visualforce pages with standard headers
- Enable clickjack protection for customer Visualforce pages with headers disabled

- (Navigation to settings: Setup > Security Controls > Session Settings)
Clickjack Protection Controls for a Site
- For Sites.com and Force.com sites pages have three options as of the Summer ’15 release:
- Allow framing by any page (no protection)
- Allow framing by same origin only (recommended)
- framing pages must have the same domain name and security protocol
- Don’t allow framing by any page (most protection)
- (Navigation to settings: Sites.com: Overview > Site Configuration; Force.com sites: Setup > Develop > Sites)
How Does a Page Look When Clickjack Protected?
- A protected page may appear in one of these ways:
- As a blank page within an iframe
- As an error message
- As a separate page
Other Stuff:
Considerations using Visualforce components on the Homepage:
Cheers!







